High-Paying Cybersecurity Jobs: Top 13 Careers
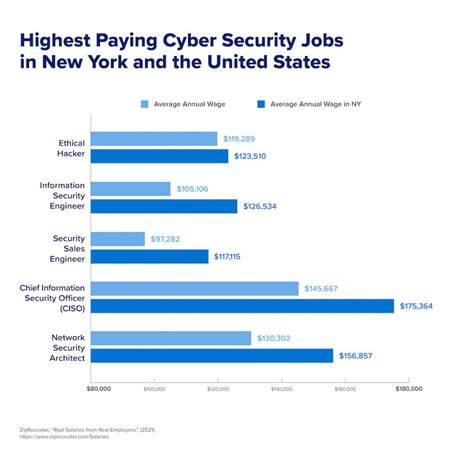
With the increasing reliance on technology and the rise in cyber threats, cybersecurity has become a critical field in the modern world. As organizations strive to protect their sensitive information and digital assets, the demand for skilled cybersecurity professionals has skyrocketed. If you are interested in a lucrative career in cybersecurity, here are the top 13 high-paying jobs to consider:
1. Chief Information Security Officer (CISO)
A Chief Information Security Officer (CISO) is a senior executive responsible for managing and overseeing an organization’s information security program. They develop and implement strategies to protect the organization’s data, systems, and networks from cyber threats. CISOs typically have extensive experience in cybersecurity and hold advanced certifications such as CISSP (Certified Information Systems Security Professional) or CISM (Certified Information Security Manager).
2. Security Architect
A Security Architect designs and builds the security infrastructure of an organization. They analyze the organization’s needs and develop comprehensive security solutions to protect against potential threats. Security Architects work closely with other IT teams to ensure that security measures are integrated into every aspect of the organization’s infrastructure.
3. Penetration Tester
Penetration Testers, also known as Ethical Hackers, are responsible for identifying vulnerabilities in an organization’s systems and networks. They simulate cyber attacks to test the effectiveness of the organization’s security controls. Penetration Testers use various tools and techniques to exploit weaknesses and provide recommendations for improving security.
4. Security Consultant
A Security Consultant provides expert advice and guidance to organizations on how to improve their security posture. They assess the organization’s current security measures, identify vulnerabilities, and recommend appropriate solutions. Security Consultants may also assist in implementing security controls and policies.
5. Incident Responder
An Incident Responder is responsible for investigating and responding to cybersecurity incidents. They analyze the nature and impact of the incident, contain the threat, and implement measures to prevent similar incidents in the future. Incident Responders work closely with other teams to minimize the impact of cyber attacks and ensure a swift recovery.
6. Cryptographer
Cryptographers specialize in creating and deciphering complex codes and encryption algorithms. They develop cryptographic systems to secure sensitive information and communications. Cryptographers play a crucial role in protecting data privacy and ensuring the integrity of digital transactions.
7. Security Engineer
A Security Engineer is responsible for designing, implementing, and maintaining an organization’s security systems. They work with other IT teams to identify vulnerabilities, implement security measures, and monitor systems for potential threats. Security Engineers also play a key role in incident response and recovery.
8. Security Analyst
Security Analysts monitor and analyze the organization’s networks and systems for security breaches or suspicious activities. They investigate alerts, conduct threat assessments, and develop strategies to mitigate risks. Security Analysts also provide recommendations for improving security controls and policies.
9. Forensic Expert
A Forensic Expert specializes in investigating cybercrimes and collecting digital evidence. They use advanced forensic tools and techniques to analyze data and trace the origins of cyber attacks. Forensic Experts work closely with law enforcement agencies and legal teams to support criminal investigations and legal proceedings.
10. Security Manager
A Security Manager oversees the organization’s security operations and policies. They develop and implement security strategies, manage security budgets, and ensure compliance with industry regulations. Security Managers also provide leadership and guidance to the cybersecurity team.
11. Security Auditor
A Security Auditor examines an organization’s security measures to ensure compliance with relevant standards and regulations. They assess the effectiveness of security controls, identify weaknesses, and provide recommendations for improvement. Security Auditors play a crucial role in ensuring that organizations meet industry best practices.
12. Cybersecurity Trainer
A Cybersecurity Trainer educates and trains employees on cybersecurity best practices. They develop training materials, conduct workshops, and create awareness campaigns to promote a security-conscious culture within the organization. Cybersecurity Trainers also stay up-to-date with the latest threats and trends in cybersecurity to deliver relevant and effective training.
13. Security Researcher
Security Researchers focus on identifying new vulnerabilities and developing innovative security solutions. They conduct in-depth research on emerging threats, analyze malware, and contribute to the development of new security technologies. Security Researchers often work in collaboration with academic institutions, security vendors, and government agencies.
Conclusion
Cybersecurity offers a wide range of high-paying career opportunities for individuals with the right skills and qualifications. As organizations continue to invest in cybersecurity to protect their valuable assets, the demand for skilled professionals in the field is expected to grow. Whether you choose to specialize in areas such as incident response, cryptography, or security architecture, a career in cybersecurity can be both financially rewarding and intellectually stimulating.
FAQs
Q: How do I get started in a cybersecurity career?
A: To start a career in cybersecurity, it is recommended to obtain a bachelor’s degree in a related field such as computer science or information technology. Additionally, gaining relevant certifications such as CompTIA Security+, CISSP, or CEH (Certified Ethical Hacker) can enhance your knowledge and credibility in the field.
Q: What skills are required for a career in cybersecurity?
A: Some essential skills for a career in cybersecurity include knowledge of networking, operating systems, programming languages, risk assessment, incident response, and cryptography. Strong problem-solving, analytical thinking, and communication skills are also valuable in the field.
Q: Is a cybersecurity career in high demand?
A: Yes, cybersecurity professionals are in high demand due to the increasing frequency and complexity of cyber threats. Organizations across various industries are seeking skilled cybersecurity experts to protect their valuable data and systems from potential attacks.
Q: What is the average salary for cybersecurity professionals?
A: The salary for cybersecurity professionals can vary depending on factors such as experience, location, and job role. However, on average, cybersecurity professionals can earn a salary ranging from $90,000 to $150,000 per year.
Q: Are there opportunities for career advancement in cybersecurity?
A: Yes, cybersecurity offers numerous opportunities for career advancement. With experience and expertise, professionals can progress to senior-level roles such as Chief Information Security Officer (CISO) or Security Consultant. Continuous learning and staying updated with the latest technologies and threats are key to advancing in the field.
